
Given the dynamic nature of the impact of Coronavirus (COVID-19), internet security should be a top priority for businesses and individuals at this time. As the virus evolves and new laws and travel bans come into effect all over the world, more and more people are starting to work from home which has unfortunately given rise to internet based scams – on both Windows and Mac.
Global emergencies, be it natural disasters, warfare or disease are dreams come true for cybercriminals – they will do all they can to take advantage of peoples’ anxiety or stress, those that are vulnerable or at high risk of being severely affected, the fear of panic buying or products being out of stock, and ‘fake news’ popping up all over social media. All of these factors lead to a huge opportunity to prey on and deceive people while they are in vulnerable positions, mentally and physically.
With this in mind, do you have an Internet and Technology Security Policy that is up to date?
An Internet and Technology Security Policy covers two key parts:
- The websites which can and cannot be used by staff.
- How and where company issued devices can be used.
Feel free to contact our team if you would like to see an example of an Internet and Technology Security Policy that you can review and even use as a starting point so you can create a robust policy for your business. We are happy to provide this free of charge and without obligation.
What do these scams look like and how are they targeting people?
Phishing – Emails such as; “Hi [staff member’s name], it’s [bosses name], can you send me the company credit card over email, I have my phone off so please don’t call me.”
Calls – People asking details about company information, your address, senior managers and accounts department email addresses etc.
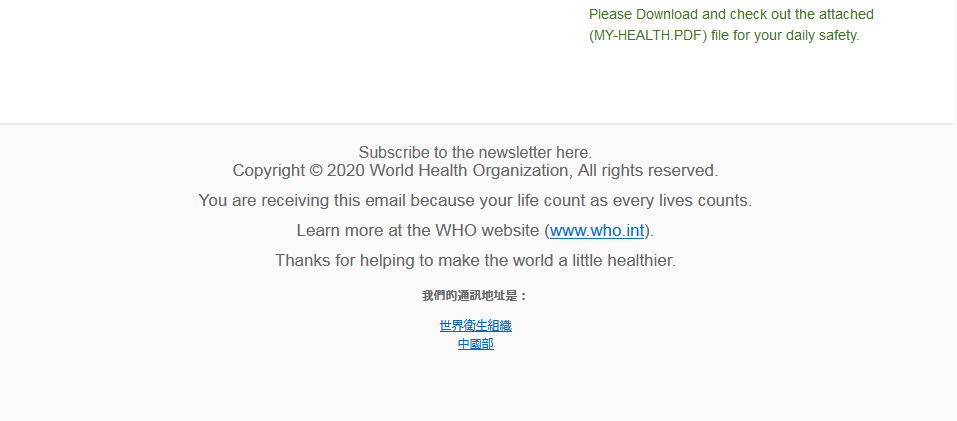
Malware or viruses in emails – These emails appear to be from the WHO, a senior member of the Government or Health industry staff, or a company seeking donations for a vaccine. See examples of these emails below.


1. It’s been common belief over the past 10 years that Macs don’t get computer ‘viruses’, however malware on Mac is now outpacing PC – according to Malwarebytes, people’s complacency is getting them into trouble as “there was a 400 percent increase in threats on Mac devices from 2018 to 2019, and found an average of 11 threats per Mac devices, which is about twice the 5.8 average on Windows”
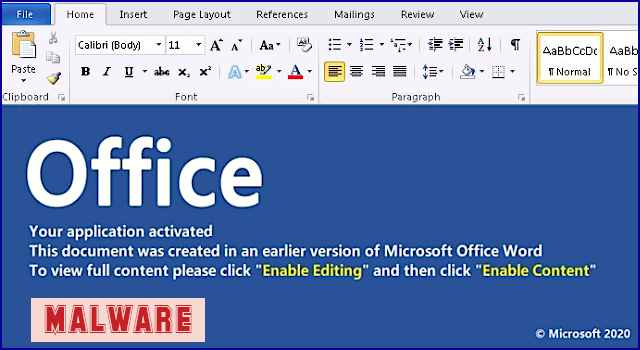
Often there are spelling errors in the subject line or come in at non standard hours of the day. Upon opening these emails and downloading attachments, malware or a keylogger (software that records keystrokes) is installed on your computer that is specifically designed to capture passwords and banking logins. These emails can contain word documents that appear innocent but contain Macro’s that allow the hackers to perform actions on your computer without your consent. They will also attempt to get you to “enable content” as by default Microsoft turns off this function for safety (see image below).
We suggest creating an approved list of email addresses that your staff can download attachments from, namely people that have emailed you before.
Malware on websites – These are designed to target people looking for information about COVID-19. According to cybersecurity firm Check Point, over 4,000 Corona or Covid related URL’s have been registered since the start of the year. These aim to attract people who are fearful of the Coronavirus and are wanting information about it. Some of these sites are simply spammy and look to sell click-bait ad placements but some are actively installing software onto users devices.
What can you and your staff do to avoid being the victim of scams?
- Have a strong password, fingerprint login, face recognition or physical thumb drive key for ALL devices that can access a company email or can login to a company or client’s website to prevent someone else logging in if the device is stolen, lost or otherwise compromised.
- Use only secure internet connections, do not use wifi that is not password protected.
- Do not visit non-approved websites on company devices (put together an approved list of sites and software)
- Do not open, download attachments from or share emails from people you do not know or from sources that are unfamiliar to you.
- Ignore any emails or calls that ask for personal information. If you have reason to believe it’s genuine, contact the supposed sender or company via a different channel than how you got the message and verify what was said with that person.
- Be cautious of emails that incite fear or further cause of alarm and encourage you to take action right away or offer vaccines or cures for the Coronavirus.
- Keep an eye out for counterfeit charities or crowdfunding campaigns.
As part of the Google Doc mentioned above, we have also included information that (once copied) you can edit and email to all of your staff regarding cybersecurity frauds, how to avoid them and what to do if they are a victim of one.
Please stay safe and take care of each other in this unprecedented time.


